What is a network?
In information technology, a computer network, also called a data network, is a series of points, or nodes, interconnected by communication paths for the purpose of transmitting, receiving and exchanging data, voice and video traffic.
Network devices including switches and routersuse a variety of protocols and algorithms to exchange information and to transport data to its intended endpoint. Every endpoint (sometimes called a host) in a network has a unique identifier, often an IP address or a Media Access Control address, that is used to indicate the source or destination of the transmission. Endpoints can include servers, personal computers, phones and many types of network hardware.

Wired and wireless technologies
Networks may use a mix of wired and wireless technologies. Network devices communicate through a wired or wireless transmission medium. In wired networks, this may consist of optical fiber, coaxial cable or copper wires in the form of a twisted pair. Wireless network pathways include computer networks that use wireless data connections for connecting endpoints. These endpoints include broadcast radio, cellular radio, microwave and satellite.
Networks can be private or public. Private networks require the user to obtain permission to gain access. Typically, this is granted either manually by a network administrator or obtained directly by the user via a password or with other credentials. Public networks like the internet do not restrict access.
Type of networks
LAN (Local area network): A local area network (LAN) is a group of computers and associated devices that share a common communications line or wireless link to a server. Typically, a LAN encompasses computers and peripherals connected to a server within a distinct geographic area such as an office or a commercial establishment. Computers and other mobile devices use a LAN connection to share resources such as a printer or network storage.
WAN (Wide Area Network): A wide area network (WAN) is a geographically distributed private telecommunications network that interconnects multiple local area networks (LANs). In an enterprise, a WAN may consist of connections to a company’s headquarters, branch offices, colocation facilities, cloud services and other facilities. Typically, a router or other multifunction device is used to connect a LAN to a WAN. Enterprise WANs allow users to share access to applications, services and other centrally located resources. This eliminates the need to install the same application server, firewall or other resource in multiple locations, for example.
WLAN (Wireless Network Technology): A wireless local area network (WLAN) is a wireless distribution method for two or more devices that use high-frequency radio waves and often include an access point to the Internet. A WLAN allows users to move around the coverage area, often a home or small office, while maintaining a network connection.
A WLAN is sometimes call a local area wireless network (LAWN).
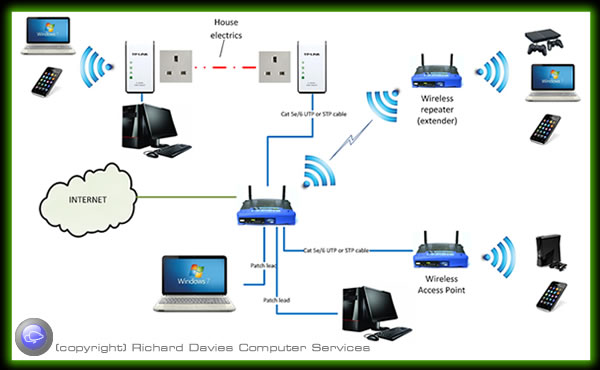
Examples of networks
PSN (PlayStation Network): PlayStation Network (PSN) is a digital media entertainment service provided by Sony Interactive Entertainment. Launched in November 2006, PSN was originally conceived for the PlayStation video game consoles, but soon extended to encompass smartphones, tablets, Blu-ray players and high-definition televisions. As of April 2016, over 110 million users have been documented, with 70 million of them active monthly.
PlayStation Network’s services are dedicated to an online marketplace (PlayStation Store), a premium subscription service for enhanced gaming and social features (PlayStation Plus), movie streaming, rentals and purchases (PlayStation Video), a cloud-based television programming service (PlayStation Vue), music streaming (PlayStation Music) and a cloud gaming service (PlayStation Now).
BEIN CONNECT: beIN Connect, also known as beIN Sports Connect, is a subsidiary over-the-top content (OTT) service launched in 2014. It allows users to watch live and on-demand video content from a Mac, Windows PC, mobile phone, Xbox 360, Xbox One, PlayStation 3 or PlayStation 4 via a broadband or Wi-Fi internet connection. On demand content comprises sports highlights, movies, and TV shows. beIN CONNECT is available as a paid service in France, Spain, United States, Canada and the MENA region

RISKS AND THREATS:
Assess risk and determine needs. When it comes to designing and implementing a risk assessment framework, it is critical to prioritize the most important breaches that need to be addressed. Although frequency may differ in each organization, this level of assessment must be done on a regular, recurring basis.
Include a total stakeholder perspective. Stakeholders include the business owners as well as employees, customers and even vendors. All of these players have the potential to negatively impact the organization (potential threats) but at the same time they can be assets in helping to mitigate risk.
Designate a central group of employees who are responsible for risk management and determine the appropriate funding level for this activity.
Implement appropriate policies and related controls and ensure that the appropriate end users are informed of any and all changes
Monitor and evaluate policy and control effectiveness. The sources of risk are ever-changing which means your team must be prepared to make any necessary adjustments to the framework. This can also involve incorporating new monitoring tools and techniques.
Malware: Malware is short for “malicious software.” Wikipedia describes malware as a term used to mean a “variety of forms of hostile, intrusive, or annoying software or program code.” Malware could be computer viruses, worms, Trojan horses, dishonest spyware, and malicious rootkits—all of which are defined below.
Computer virus: A computer virus is a small piece of software that can spread from one infected computer to another. The virus could corrupt, steal, or delete data on your computer—even erasing everything on your hard drive. A virus could also use other programs like your email program to spread itself to other computers.
Rogue security software: Have you ever seen a pop-up window that advertises a security update or alert? It appears legitimate and asks you to click on a link to install the “update” or “remove” unwanted malicious software that it has apparently detected. This could be rogue security software designed to lure people into clicking and downloading malicious software. Microsoft has a useful webpage that describes rogue security software and how you can protect yourself.
Trojan horse: Users can infect their computers with Trojan horse software simply by downloading an application they thought was legitimate but was in fact malicious. Once inside your computer, a Trojan horse can do anything from record your passwords by logging keystrokes (known as a keystroke logger) to hijacking your webcam to watch and record your every move.
Malicious spyware: Malicious spyware is used to describe the Trojan application that was created by cybercriminals to spy on their victims. An example would be keylogger software that records a victim’s every keystroke on his or her keyboard. The recorded information is periodically sent back to the originating cybercriminal over the Internet. Keylogging software is widely available and is marketed to parents or businesses that want to monitor their kids’ or employees’ Internet usage.
Computer worm: A computer worm is a software program that can copy itself from one computer to another, without human interaction. Worms can replicate in great volume and with great speed. For example, a worm can send copies of itself to every contact in your email address book and then send itself to all the contacts in your contacts’ address books.
Botnet: A botnet is a group of computers connected to the Internet that have been compromised by a hacker using a computer virus or Trojan horse. An individual computer in the group is known as a “zombie“ computer.
Spam: Spam in the security context is primarily used to describe email spam —unwanted messages in your email inbox. Spam, or electronic junk mail, is a nuisance as it can clutter your mailbox as well as potentially take up space on your mail server. Unwanted junk mail advertising items you don’t care for is harmless, relatively speaking. However, spam messages can contain links that when clicked on could go to a website that installs malicious software onto your computer.
Phishing: Phishing scams are fraudulent attempts by cybercriminals to obtain private information. Phishing scams often appear in the guise of email messages designed to appear as though they are from legitimate sources. For example, the message would try to lure you into giving your personal information by pretending that your bank or email service provider is updating its website and that you must click on the link in the email to verify your account information and password details.
Rootkit: According to TechTarget, a rootkit is a collection of tools that are used to obtain administrator-level access to a computer or a network of computers. A rootkit could be installed on your computer by a cybercriminal exploiting a vulnerability or security hole in a legitimate application on your PC and may contain spyware that monitors and records keystrokes.

