DEFINITION OF ANTIVIRUS:
Antivirus software is a class of program designed to prevent, detect and remove malware infections on individual computing devices, networks and IT systems.Antivirus software, originally designed to detect and remove viruses from computers, can also protect against a wide variety of threats, including other types of malicious software, such as keyloggers, browser hijackers, Trojan horses, worms, rootkits, spyware, adware, botnets and ransomware.
BITDEFENDER:
This award-winning anti-malware solution has been recognized by experts and users for its unparalleled virus detection.
Bitdefender Antivirus Plus 2017 is amazingly powerful and efficient. It protects from viruses, worms and Trojans, ransomware, zero-day exploits, rootkits and spyware. Your data and your privacy are in good hands.
Bitdefender Antivirus Plus takes care of all digital threats, so you can enjoy the peace of mind that you deserve. What you get:
- Best antivirus protection against all e-threats
- Superior performance with no slowdowns
- Wi-Fi Security Advisor. Always secure on the go
- Single-touch security. Advanced automatic protection
ADVANTAGES
- Autopilot mode allows to work with computer without interruptions and slowdowns, all protection functions are being performed automaticly;
- spam filter high efficiency;
- protected browser;
- firewall effectively stands against direct targeted attacks;
- social network security, privacy setting ups control.
DISADVANTAGES
- Firewall default settings has some negative protection measures;
- system performance average influence;
- some difficulties with installation on infected systems;
- functionally limited password manager.

PANDA
According to Panda Security, Panda Cloud Antivirus is able to detect viruses, trojans, worms, spyware, dialers, hacking tools, hacker and other security risks.
Panda Cloud Antivirus relies on its “Collective Intelligence” and the cloud for up-to-date information.
ADVANTAGES
1. Good Detection rate
2. Low memory usage
3. Web protection
4. Collective intelligence
5. Good program configuration
6. Good behavioural analysis
7. Improve handling of hardware resources
DISADVANTAGES
1. Slow scan
2. Some removal issues
3. Dependant on internet connection (weaker offline protection)
4. Heavy on system for a cloud program
5. Some false positives despite information available in the cloud
NORTON
Norton AntiVirus is an anti-malware software developed and distributed by Symantec Corporation since 1991 as part of its Norton family of computer security products. It uses signatures and heuristics to identify viruses. Other features included in it are e-mail spamfiltering and phishing protection.
ADVANTAGES:
Experience: Norton has been around since the primary versions of Windows and Macintosh. It has evolved accordingly along with all versions of operating systems to deal with software, codes and procedures which have ill intentions in circulation over internet.
Sensible and fast: Norton’s virus definitions are cloud based and are quick responsive. In that, malicious URL blocking is an excellent feature and scored high in antiphishing test.
Cross platform protection: Norton has security solutions for computers running on different platforms like Windows, Mac OS, Android, and iOS and simultaneously protects 10 devices from some of the worst Internet predators. The Norton Antivirus Customer service ensures that the clients make the best use of the software.
Security features: The software has security features like smart firewall, Spam filtering, Password management and Performance optimization which ensure safety from malicious attachments received from strangers or even friends.
Online backup: It offers 25GB online backup to its users. Any issue related to this does not need Norton technical support and is simple to be resolved.
Parental Control: One of the remarkable features is its Award-winning parental control. It gives complete freedom to parents to control and protect their child’s exposure to internet.
DISADVANTAGES
Demanding on Resources (Size): It takes up plenty of laptop resources to do its job. If one has Norton on a computer run for many years, you would observe slowed down overall performance of the computer. It is also noticed that your computer runs considerably quicker without Norton. Norton technical support is not a destination anyway as this is an inherent issue.
Un-installation Problems: If you attempt to remove Norton Antivirus, the un-installation process proves difficult. Rather than wiping the computer clean of the program, traces of it continue to linger on the hard drive.

MCAFEE
McAfee, Inc. (known as Intel Security Group in 2014–2017) is an American global computer security software company headquartered in Santa Clara, California and claims to be the world’s largest dedicated security technology company.
The company was purchased by Intel in February 2011, and became part of the Intel Security division.
On September 7, 2016, Intel announced a strategic deal with TPG Capital to convert Intel Security into a joint venture between both companies called McAfee.That deal closed on April 3, 2017. Thoma Bravo took a minority stake in the new company, and Intel maintains a 49% stake.
ADVANTAGES
Decent Price: McAfee offers wide range of features at the price offered. It has a satisfactory security portfolio assuring many users at a best price. McAfee Antivirus Customer Service is the best platform to know the prices of its diversified products.
Regular updates: McAfee comes up with new versions at regular intervals so that the users’ protection software has the most advanced virus database to give protection from latest malicious codes and viruses. The whole updates and maintenance procedures are done in the background without the user having to deal with the ongoing tasks of the PC.
Affordable and cheap: McAfee is comparatively cheaper over its other counterparts and the detection rate is still at the top of the charts. As there are other antivirus software with greater detection rates, McAfee is quiet enough to keep the viruses away at such a price.
DISADVANTAGES
Comparisons and tests held by TopTenReviews.com analyzed that McAfee antivirus that it is not the fastest program amongst the similar programs as it takes a huge memory be it a scan or a real time protection.
The scan duration is quite long and the memory used to scan is high. If the antivirus program eats little memory during scanning, the user will have options to multi task while the scanner is on.
As the memory usage is too high, the user may have to leave the PC until the scan gets completed preventing the user from accessing the computer. However, all the memory concerns are solved by the McAfee customer support.
As the McAfee antivirus is favorite to many users despite its little disadvantages, the software is quiet competitive to many of its counterparts in its speed and response.

AVAST
Avast is a Czech multinational cybersecurity software company headquartered in Prague, Czech Republic. Avast has more than 400 million users and the largest market share among anti-malware application vendors worldwide. The company has more than 1,000 employees, with about 650 at its headquarters in the Czech Republic. Avast was founded by Pavel Baudiš and Eduard Kučera in 1988 as a cooperative and has been a private company since 2010.
Avast is at the top of the antivirus market share with 20.5%, as of June 2017. In July 2016, Avast acquired competitor AVG Technologies for $1.3 billion, at the time it was the third-ranked product.
ADVANTAGES
- Really light on the system
- Modern and neat UI
- Fully customizable installer: can select features to install
- Hardened mode to block all unknown programs
- Lots of features and components to tweak
- Good detection capability with supporting secondary components
DISADVANTAGES:
- Many ad’s and pop-up’s
- Default setup is bloated
- Need an account to use the product after 1 month
- Need an anti-ransom ware module
- DeepScreen is not good enough and disabled by default
- Unintuitive Settings UI, HIPS module needs to improve (remember option necessary)
- Ads in web plugin and has a long way to go (not great at the moment)
- Not great signatures for real-world protection
- Cloud reputation needs improvement

AVG
AVG (AntiVirus Guard) es un software antivirus desarrollado por la empresa checa, AVG Technologies, disponible para sistemas operativos Windows, Linux, Android, iOS y Windows Phone, entre otros. Actualmente este software de antivirus en todas sus versiones es propiedad de Avast.
ADVANTAGES
1. AVG Installation is quite easy
2. Auto update over online ( Schedule Update )
3. AVG can be installed on the Mozilla Firefox browser as a plugin so it is safer surfing
4. Virus scanning is faster
5. Memory used on the PC is not too much
6. Resident option does not slow down computer performance
7. Fiture have Anti-Spyware, Link-Scanner, Email Scanner
8. Anti Spam
DISADVANTAGES
1. To AVG lates version ( AVG 9 ) The first installation is quite long
2. Setting operation is rather complicated
3. file that the virus was removed by usual along with the AVG Virus
4. AVG usually rely on computer operating systems used
5. AVG sometimes assume .exe file as a virus, especially in crack
6. Update antivirus longer


:max_bytes(150000):strip_icc()/wifi-password-57f560ef5f9b586c359127f9.png)












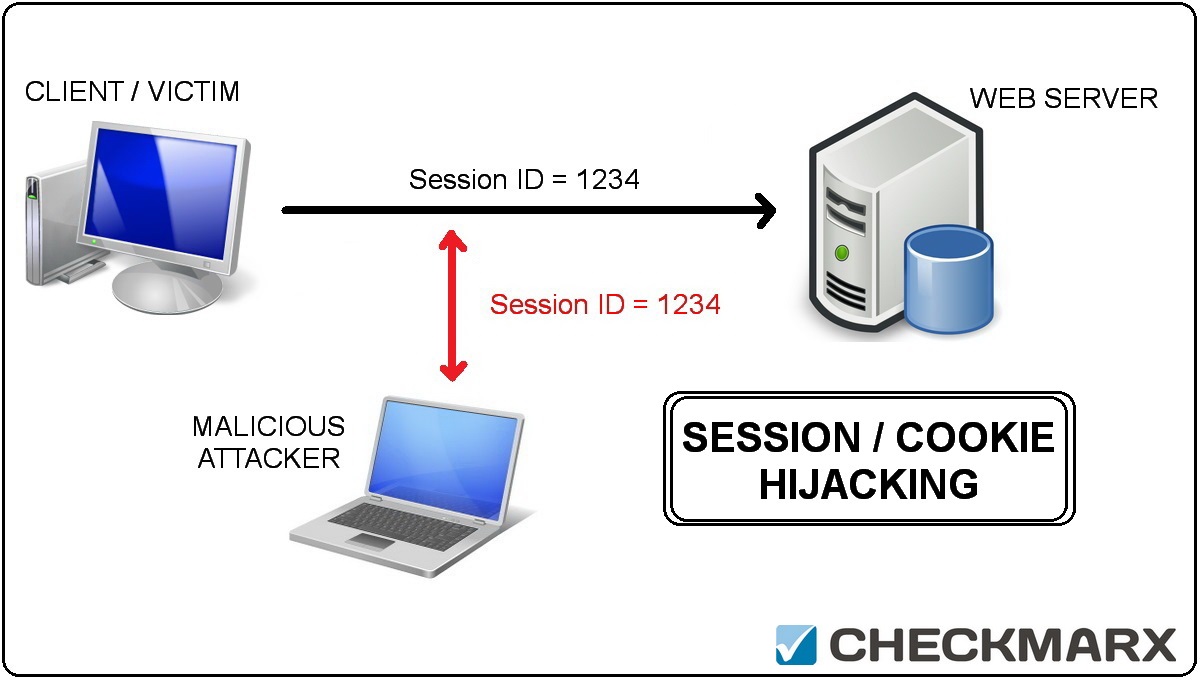
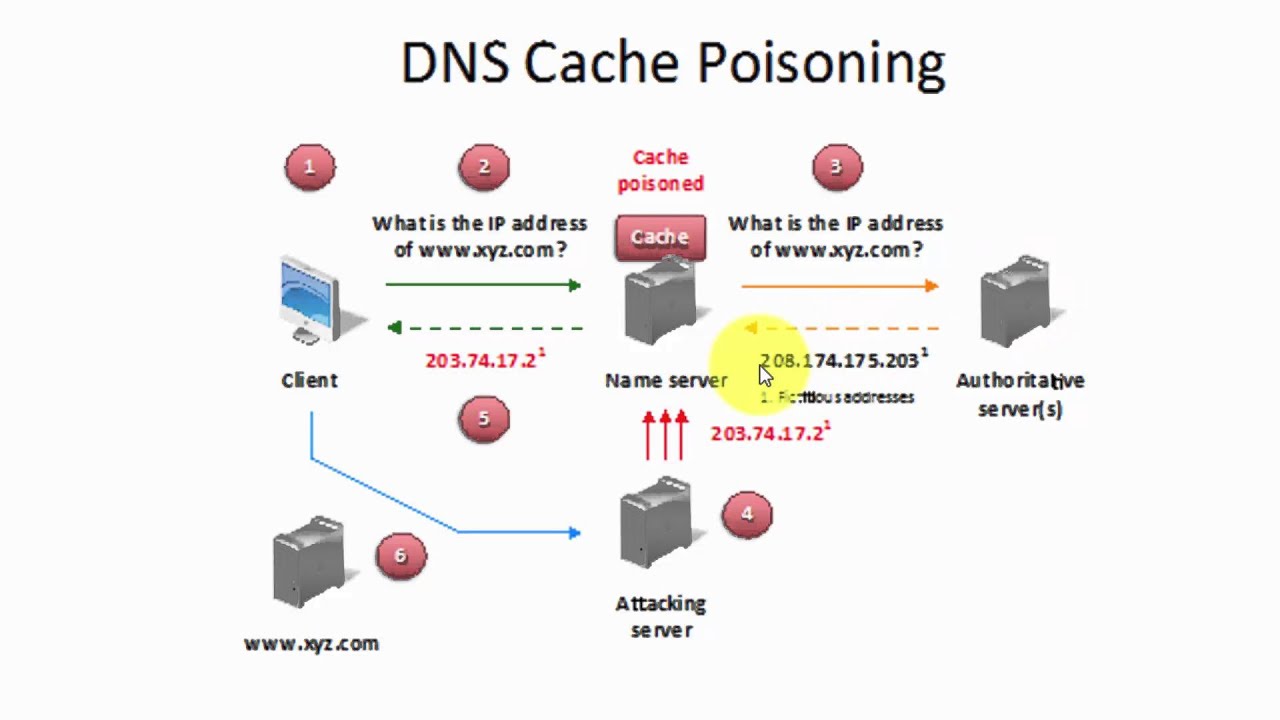















 easy passwords in few minutes. One recent study showed that a 6 character password with all lower case letters can be broken in under 6 minutes!
easy passwords in few minutes. One recent study showed that a 6 character password with all lower case letters can be broken in under 6 minutes!